Your WordPress Security is Horrible – Here’s How to Fix It - Six Revisions |
| Your WordPress Security is Horrible – Here’s How to Fix It Posted: 04 Mar 2015 06:30 AM PST You’ve probably heard plenty of horror stories about security problems involving WordPress sites (such as this one and this one), and they may have gotten you worried. The truth is, we could all implement additional measures for securing our WordPress installs. Here are five things you can do today to greatly enhance the security of your WordPress-powered sites.
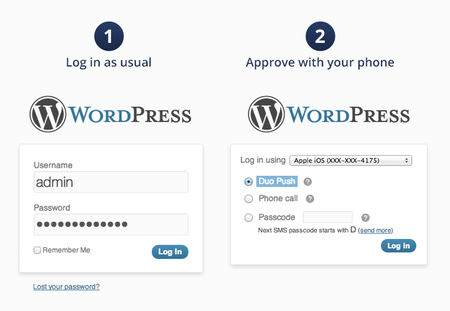
Secure Your Admin AreaEven if you have a random username and strong password for accessing the WordPress administration area, using additional layers of authentication is a good idea because they can lower the chance of a brute-force attack becoming successful. There are three options for strengthening the security of the WordPress admin area. Option 1: Password-Protect the WordPress Login PageOn an Apache web server, you can use htpasswd, which is a simple method of password-protecting website files. (Nginx, IIS, and other web servers will have their own version of password-protection.) For WordPress, you could password-protect the To learn how to password-protect your WordPress admin area, read this tutorial. Option 2: Set Up Two-Step VerificationTwo-step verification requires two separate stages of authentication before you can log into your WordPress admin area. This additional layer of authentication helps secure your WordPress site in cases where your username and password have been compromised without your knowledge. Two-step verification can give you time to reset your login information before your WordPress admin area is breached. Two-step verification also informs you when there are attempts to log into your WordPress admin area. Here’s how two-step verification works:
You can use the Google Authenticator for WordPress plugin in conjunction with the Google Authenticator (which is available on iOS, Android and Blackberry devices). Another plugin to consider is Duo Two-Factor Authentication. It can be set up to send an SMS to your mobile phone or to perform a voice call that discloses your unique password.
Option 3: IP Address WhitelistingUsing this option, only authorized (whitelisted) IP addresses can access the WordPress admin area. A drawback with IP address whitelisting is, if you work in many places (coffee shops, coworking spaces, etc.) or if you travel frequently, this security measure can be a hassle since you’d have to whitelist the IP address you’re using before you can access your admin area. There are workarounds to this, such as using a VPN so that you have a static IP address regardless of which network you’re connecting from. Whitelisting IP addresses can be done through your site’s If you want to whitelist multiple IP addresses, just add additional Maintain a Good Password PolicyWordPress sites involve several services that have user authentication: Your MySQL database, graphical user interfaces that you use to manage your WordPress-related assets and hosting such as cPanel and phpMyAdmin, the WordPress admin area, etc. It’s best to use strong, randomly-generated passwords for all services that can potentially be exploited to affect your WordPress site. Also, it’s a good practice never to use the same username and password credentials for different services. This way, if one of your login credentials is compromised, the breach can be contained to just one service. Using a password manager such as LastPass can help you keep track of your passwords. Because a password manager remembers your passwords for you, it gives you the freedom to choose complex (and thus more secure) passwords that you don’t have to commit to memory. Remove Website Files That You Don’t NeedHaving a regular website maintenance routine where you remove unused and outdated website files can improve WordPress security because doing so reduces potential attack vectors. Many people either forget to remove unused or outdated files, or don’t think these files can be harmful and so they don’t take the time to maintain them. Later on, these files can cause security problems such as cross-site contamination, where attackers exploit vulnerabilities in old files that you’ve forgotten about. Here’s a list of things to remove:
Protect Your WordPress Site Against DDoS AttacksDistributed denial-of-service (DDoS) attacks are attacks that attempt to crash your website. Many people don’t think they can be a target of a DDoS attack, but it can happen to anyone. With regular reports and studies showing that DDoS attack frequency, duration and size are growing drastically, now is the time to take steps to defend your site against downtime and subsequent revenue loss caused by denial-of-service. Here are some services to look into if you’re concerned about DDoS attacks: Use a Web Application FirewallNo matter how big (or small) your WordPress site is, it needs a web application firewall. A web application firewall blocks attacks that attempt to exploit common security vulnerabilities. Even if you’re keeping your WordPress install, theme and plugins up-to-date with the latest security patches, you’re still at risk of exposure to zero-day attacks. Zero-day attacks in the context of WordPress can come from things like unpatched security issues that are unknown to the developers of your plugins or theme, or security issues that the developers have had no time to fix and release a patch for. A web application firewall could significantly reduce zero-day-attack vulnerabilities by blocking commonly known exploits such as SQL injection and XSS. If you run your own Apache web server (or are using a VPS), ModSecurity is a free and open source web application firewall module you can install. If you have a bit of money to spend, check out CloudProxy, a suite of website protection software. It comes with a web application firewall that supports many types of publishing platforms, including WordPress. If you’re on a shared web hosting service and have a restricted ability to configure your web server, have a look at the Block Bad Queries WordPress plugin. While it isn’t technically a web application firewall, it does a good job of blocking malicious requests. BBQ adds directives to your Related Content
About the AuthorThe post Your WordPress Security is Horrible – Here’s How to Fix It appeared first on Six Revisions. |
| You are subscribed to email updates from Six Revisions To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |

No comments:
Post a Comment